So it is big in the news this week, ROCA, what’s the deal?
I’m not going to cover this in detail yet, however here is what you need to know now:
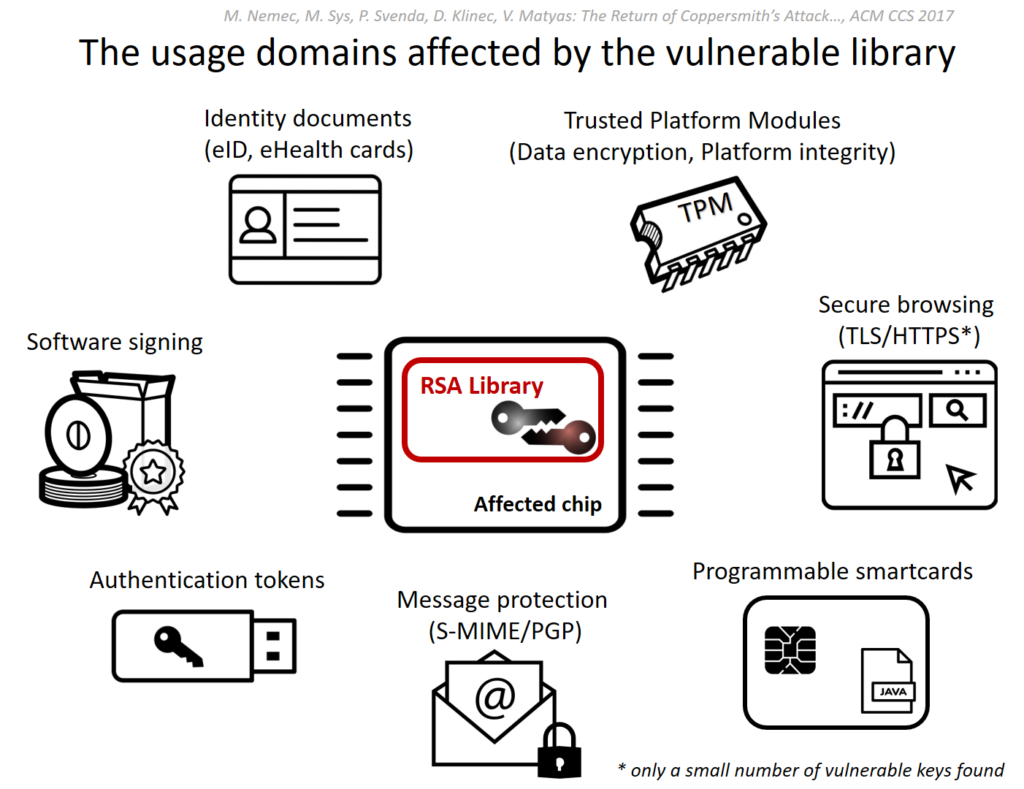
The ROCA vulnerability (tracked as CVE-2017-15361) enables computation of RSA private keys from their public certificate/key counterparts. The flaw affects the implementation of RSA key pair generation by Infineon’s Trusted Platform Module (TPM). It is possible for a range of key lengths, including commonly used 2048 bit and older 1024 bit certificates. Chips as early as 2012 are affected and these are common place in TPM v1.1 modules.
Source: https://crocs.fi.muni.cz/public/papers/rsa_ccs17
A successful computation of a private key allows, depending on its use, the attacker to decrypt sensitive data (eg: file encryption, disk encryption, HTTPS), forging digital signatures (used for email security, and file signing), or even impersonation and identity theft from (access control cards to e-ID cards).
Major vendors including Microsoft, Google, HP, Lenovo, Fujitsu already released the software updates and guidelines for a mitigation.
The ‘The Return of Coppersmith’s Attack: Practical Factorization of Widely Used RSA Moduli’ (ROCA) research paper will be released at ACM CCS in 2 weeks time.
Recommended Reading & Tools (Online and Offline)
- ROCA: Infineon RSA vulnerability Detection Tool – https://github.com/crocs-muni/roca
- More Reading – https://crocs.fi.muni.cz/public/papers/rsa_ccs17
- KeyChest ROCA Vulnerability Test Suite – https://keychest.net/roca